What is AWS KMS?
AWS KMS is a managed service that enables you to create, control, and use encryption keys to protect data across your applications. By leveraging AWS KMS, businesses can confidently manage data encryption with a variety of flexible tools and practices. Here’s a breakdown of the key components and functionalities of AWS KMS.
What are KMS Keys?
KMS keys are central to AWS KMS’s operations. They are cryptographic keys used for data encryption and decryption. Each KMS key has its own unique characteristics:
• Symmetric KMS Keys: These are 256-bit Advanced Encryption Standard (AES) keys, used for both encrypting and decrypting data and cannot be exported from AWS KMS.
• Data Keys: Data keys can encrypt larger volumes of data. AWS KMS can generate and encrypt these keys, though it doesn’t store or manage them directly.
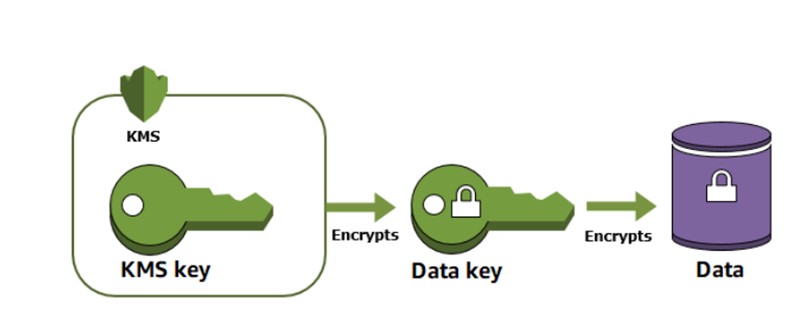
Source: https://docs.aws.amazon.com/kms/latest/developerguide/overview.html
Why Use AWS KMS?
When you encrypt data, you need to protect your encryption key. If you encrypt your key, you need to protect its encryption key. Eventually, you must protect the highest-level encryption key (known as a root key) in the hierarchy that protects your data. That’s where AWS KMS comes in.
AWS KMS protects your root keys. KMS keys are created, managed, used, and deleted entirely within AWS KMS. They never leave the service unencrypted.
Additionally, you can create and manage key policies in AWS KMS, ensuring that only trusted users have access to KMS keys.
Key Features of AWS KMS:
• Key Creation and Management: You can easily create and manage various types of cryptographic keys, including symmetric keys and asymmetric key pairs.
• Key Rotation: KMS supports automatic key rotation, which helps to enhance security by minimizing the lifetime of keys.
• Key Usage Restrictions: You can define specific usage restrictions for your keys, such as limiting them to certain AWS services or requiring additional authentication factors.
• Centralized Key Management: KMS allows you to manage all of your cryptographic keys from a single location, simplifying key management tasks.
• Integration with AWS Services: KMS integrates seamlessly with many AWS services, such as Amazon S3, Amazon RDS, and Amazon EBS, making it easy to encrypt data at rest.
• Compliance and Auditing: KMS helps you meet compliance requirements by providing features such as key audit logs and access controls.
• HSM-Based Key Protection: KMS offers HSM-based key protection, which provides an additional layer of security for sensitive data.
Key Benefits of Using AWS KMS:
• Enhanced Security: KMS helps to protect your data by providing strong encryption and key management capabilities.
• Simplified Key Management: KMS streamlines the process of creating, managing, and controlling access to cryptographic keys.
• Improved Compliance: KMS can help you meet compliance requirements by providing features such as key audit logs and access controls.
• Cost-Effective: KMS is a cost-effective solution for managing cryptographic keys.
• Scalability: KMS can scale to meet the needs of your growing business.
Types of KMS Keys
AWS KMS provides three types of KMS keys to suit different security needs:
• Customer Managed Keys: You create and control these keys, customizing policies and permissions. This control extends to managing key rotations, setting up aliases, and even scheduling deletions.
• AWS Managed Keys: These are managed by AWS on behalf of a specific AWS service, though they cannot be directly managed or used outside that service.
• AWS Owned Keys: AWS owns and manages these keys across multiple accounts, making them inaccessible for direct management or auditing by customers.
How Does AWS KMS Encrypt Data?
AWS KMS employs several methods for data encryption:
Data Keys and Envelope Encryption
In envelope encryption, data is first encrypted with a data key, which is then encrypted by a KMS key known as the root key. This two-layer encryption ensures an additional level of security.
Encryption Context
KMS operations accept an optional encryption context, a set of key-value pairs providing additional information about the data being encrypted. This helps add context to the encrypted data, making it easier to identify and validate in future processes.
Managing AWS KMS Keys and Access
Managing access to KMS keys is critical for security, especially when multiple teams or departments are involved. Here are some key components for effective key management:
• Key Policies and Grants: Permissions to access KMS keys are managed through key policies. Alternatively, temporary access can be granted using grants, which can be applied, utilized, and revoked as needed without affecting long-term permissions.
• Grant Tokens: To mitigate delays in grant permissions due to eventual consistency, grant tokens can be used for faster access rights activation.
Custom Key Stores and VPC Integration
For highly sensitive data, AWS KMS allows integration with AWS CloudHSM (Hardware Security Module) clusters through custom key stores. A custom key store provides a dedicated, secure storage location for cryptographic keys.
Additionally, KMS allows you to connect directly through a private VPC endpoint, ensuring that all communication between your Virtual Private Cloud (VPC) and AWS KMS remains within the AWS network, bypassing the public internet for added security.
Rotating, Importing, and Deleting KMS Keys
Managing the lifecycle of encryption keys is a vital aspect of data security. AWS KMS provides several features to handle key management effectively:
• Key Rotation: AWS KMS can automatically rotate customer-managed KMS keys annually, maintaining historical key material for decryption purposes.
• Importing Keys: Businesses can import their own key material to AWS KMS, with options to set expiration dates or delete key material on demand.
• Deleting Keys: When a KMS key is deleted, all associated metadata and key material are removed, making it impossible to decrypt any data previously encrypted with that key. AWS KMS also offers the ability to disable keys temporarily if access restrictions are needed.
Monitoring Key Usage with CloudWatch
To ensure robust monitoring, AWS KMS integrates with CloudWatch to track key usage and send notifications when certain actions are taken. For instance, you can create a CloudWatch alarm that triggers an alert if someone tries to use a key that’s pending deletion.
AWS KMS is an indispensable tool for organizations needing to secure sensitive data efficiently. By understanding KMS keys, managing access, and leveraging encryption best practices, companies can create a reliable data protection framework that scales with their needs.
AWS + Beinex Partnership: How Can We Help You
Beinex is proud to be an AWS consulting partner dedicated to empowering our customers with AWS-managed services to host their BI solutions and beyond in the cloud. Our cloud migration experts deliver top-tier stability and reliability by aligning with your business strategy and collaborating closely to implement AWS infrastructure as a service.
Experience AWS for free: https://beinex.com/beinex-amazon-web-services/